Share this infographic on your site!
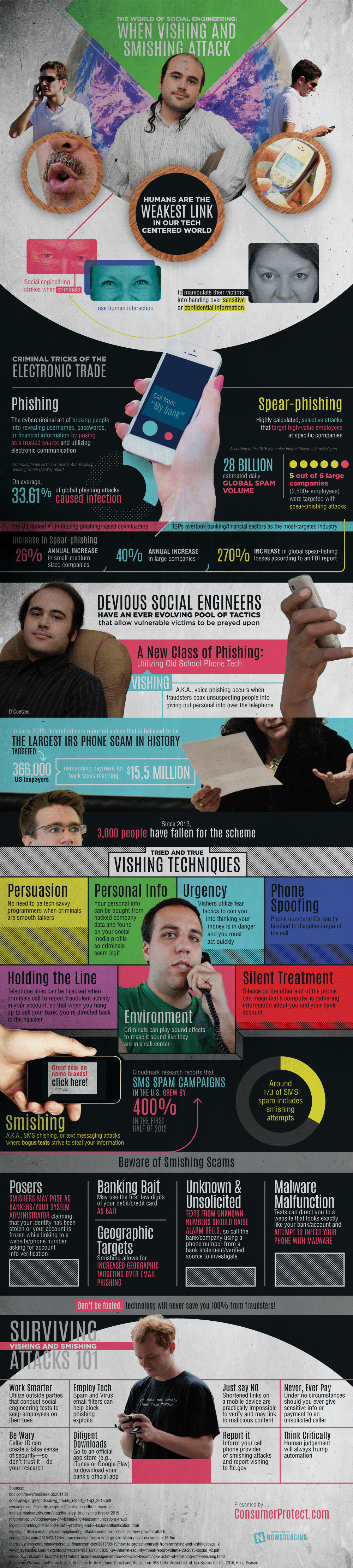
Humans Are the Weakest Link in our Tech Centered World
- Criminal Tricks of the Electronic Trade
- Phishing: The cybercriminal art of tricking people into revealing usernames, passwords, or financial information by posing as a trusted source and utilizing electronic communication
- According to the 2015 1-3 Quarter Anti-Phishing Working Group (APWG) report
- On average, 33.61% of global phishing attacks caused infection
- The US ranked #1 in hosting phishing-based downloaders
- ISPs overtook banking/financial sectors as the most-targeted industry
- According to the 2015 Symantec Internet Security Threat Report
- 28 billion estimated global spam volume per day
- 5 out of 6 large companies (2,500+ employees) were targeted with spear-phishing attacks
- 40% annual increase for large companies
- 26% annual increase in small-medium sized companies
- Spear-phishing: Highly calculated, selective attacks that target high-value employees at specific companies
- 2015: FBI reports showed a 270% increase in global spear-fishing losses
- According to the 2015 1-3 Quarter Anti-Phishing Working Group (APWG) report
- Phishing: The cybercriminal art of tricking people into revealing usernames, passwords, or financial information by posing as a trusted source and utilizing electronic communication
- A New Class of Phishing: Utilizing Old School Phone Tech
- Vishing: K.A., voice phishing occurs when fraudsters coax unsuspecting people into giving out personal info over the telephone
In early 2015, federal officers reported that what is believed to be the largest IRS phone scam in history, targeted 366,000 US taxpayers, demanding payment for back taxes reaching $15.5 million
- Since 2013, 3,000 people have fallen for the scheme
- Tried and true vishing techniques
- Persuasion: No need to be tech savvy programmers when criminals are smooth talkers
- Personal Info: Your personal info can be bought from hacked company data and found on your social media profile so criminals seem legit
- Urgency: Vishers utilize fear tactics to con you into thinking you’re money is in danger and you must act quickly
- Phone Spoofing: Phone numbers/IDs can be falsified to disguise origin of the call
- Holding the Line: Telephone lines can be hijacked when criminals call to report fraudulent activity in your account, so that when you hang up to call your bank, you’re directed back to the hijacker
- Environment: Criminals can play a sound effects CD to make it sound like they are in a call center
- Silent Treatment: Silence on the other end of the phone can mean that a computer is gathering information about you and your bank account
- Smishing: A.K.A., SMS phishing, or text messaging attacks, where bogus texts strive to steal your information
Cloudmark research reports that SMS spam campaigns in the U.S. grew by 400% in the first half 2012, and around ⅓ of SMS spam includes smishing attempts
- Beware of Smishing Scams
- Posers: Smishers may pose as bankers/your system administrator claiming that your identity has been stolen or your account is froze while linking to a website/phone number asking for account info verification
- Banking Bait: May use the first few digits of your debit/credit card as bait
- Malware Malfunction: Texts can direct you to a website that looks exactly like your bank/account and attempt to infect your phone with malware
- Unknown & Unsolicited: Texts from unknown numbers should raise alarm bells, so call the bank/company using a number from a bank statement/verified source to investigate
- Geographic Targets: Smishing allows for increased geographic targeting over email phishing
Don’t be fooled, technology will never save you 100% from fraudsters!
- Surviving Vishing and Smishing Attacks 101
- Work Smarter
- Utilize outside parties that conduct social engineering tests to keep employees on their toes
- Employ Tech
- Spam and Virus email filters can help block phishing exploits
- Be Wary
- Caller ID can create a false sense of security—so don’t trust it—do your research
- Diligent Downloads
- Go to an official app store (e.g., iTunes store or Google Play store) to download your bank’s official app
- Just say NO
- Shortened links on a mobile device are practically impossible to verify and may link to malicious content
- Never, Ever Pay
- Under no circumstances should you ever give sensitive info or payment to an unsolicited caller
- Report it
- Inform your cell phone provider of smishing attacks and report vishing to ftc.gov
- Think Critically
- Human judgement will always trump automation
- Work Smarter





